

Telegram Scams: 11 Fraud Schemes To Watch Out For

Let’s talk about the Telegram scams. With over 700 million monthly active users, Telegram has emerged as a leading messaging app, offering a seamless and secure communication platform. However, its popularity hasn’t escaped the attention of scammers, who have found ways to exploit its vast user base.
Much like the familiar scams you encounter daily in the form of fake text messages, phishing emails, and pesky robocalls, Telegram scams also rely on cunning social engineering tactics. Their ultimate goal is to pry sensitive information from you, such as credit card details, Social Security numbers (SSN), or even precious two-factor authentication (2FA) codes for cryptocurrency and social media accounts.
In this article, we’ll shed light on the most prevalent Telegram app scams that demand your vigilance. Armed with insights and actionable advice, you’ll be able to discern a Telegram imposter from a legitimate friend or contact confidently.
What are Telegram scams?
Telegram scams are deceptive schemes orchestrated by malicious individuals on the Telegram messaging app to trick and defraud users. These scams aim to extract personal information, financial details, or even cryptocurrency from unsuspecting victims.
Here are some of the most typical Telegram scam schemes to watch out for.
- Phishing scams. Scammers create fake login pages or websites that imitate legitimate services to steal your login credentials or personal information.
- Fake giveaways. Imposters pose as well-known personalities or companies, promising free giveaways or cryptocurrency in exchange for a small initial payment. However, they never deliver on their promises.
- Pump and dump crypto schemes. Scammers promote low-value cryptocurrencies as “hot” investments, urging users to buy them and artificially inflate their prices. Once the price rises, they sell their holdings, leaving others at a loss.
- Impersonation scams. Scammers pretend to be someone you know or trust, like a friend, family member, or official organization and request money or sensitive information.
- Malware distribution. Scammers share seemingly harmless files that contain malware, aiming to compromise your device and steal personal data.
These are just a few examples but in reality, scammers are much more shifty and have a lot more tricks up their sleeve. But fear not, as we’re here to equip you with the knowledge and tools necessary to identify and evade these threats effectively. Let’s move on.
Why Telegram is so popular among fraudsters?
Telegram has gained popularity among fraudsters for several key reasons.
Anonymity and pseudonymity
Telegram allows users to create accounts without providing real names or personal information, enabling fraudsters to maintain anonymity. This makes it easier for them to create fake profiles and conduct scams without fear of immediate identification.
End-to-end encryption
Telegram boasts robust end-to-end encryption for messages, providing a secure communication channel. While encryption benefits users’ privacy and security, it also attracts fraudsters who can exploit this feature to avoid detection and intercepting of their messages.
Large user base
With over 700 million monthly active users, Telegram provides fraudsters with a vast pool of potential victims. A large user base offers greater anonymity for scammers and increases their chances of finding susceptible targets.
Ease of use and convenience
Telegram’s user-friendly interface and straightforward messaging system make it an accessible platform for everyone, including fraudsters. They can quickly create accounts, send messages, and launch scams without significant technical expertise.
File sharing and media capabilities
Telegram allows users to share files, images, and videos, providing scammers with a means to distribute malware and fraudulent content discreetly. This feature can be exploited to deceive users into downloading harmful files or visiting malicious websites.
Global reach
Telegram is popular worldwide and available in multiple languages, making it an attractive platform for international fraud operations. Fraudsters can target users from different regions and time zones, making it challenging for law enforcement to combat these scams effectively.
Limited content moderation
Compared to some other messaging apps, Telegram has been criticized for its relatively lenient content moderation policies. While this approach aims to prioritize user privacy, it can inadvertently allow fraudsters to exploit the platform for illegal activities.
Bot functionality
Telegram’s bot functionality allows users to interact with automated accounts. While bots can serve useful purposes, such as customer support, they can also be used by fraudsters to disseminate spam, phishing links, and other malicious content.
It’s important to recognize that while Telegram’s features have attracted fraudsters, the platform itself remains an amazing communication tool with numerous cool features and possibilities. The responsibility lies with both users and platform operators to stay vigilant, report suspicious activities, and implement security measures to protect against scams and other fraudulent activities, ensuring a safer and enjoyable experience for all legitimate users.
11 Telegram scam schemes to be cautious about
Phishing scams
Phishing scams on Telegram involve scammers creating fake login pages or websites that closely resemble legitimate platforms or services. They often send links through messages, enticing users to click on them. Once users enter their login credentials on these fake pages, scammers gain access to their accounts, putting sensitive data at risk.
How to recognize it and protect yourself
- Always double-check URLs before clicking on any links, especially those received from unknown sources.
- Be cautious of unsolicited messages asking you to log in or provide personal information.
- Enable two-factor authentication (2FA) for an extra layer of security.
Fake giveaways
In this scam, fraudsters pretend to be well-known personalities, influencers, or reputable companies offering free giveaways or cryptocurrency rewards. To participate, users are asked to send a small amount of cryptocurrency as an entry fee. However, the promised giveaway never materializes, and users lose their money.
How to recognize and protect yourself
- Be skeptical of offers that sound too good to be true.
- Verify the authenticity of giveaways by checking the official social media accounts or websites of the involved parties.
- Never send money or personal information to participate in giveaways.
Pump-and-dump schemes
Pump-and-dump schemes involve scammers promoting low-value cryptocurrencies as the next big thing. They encourage users to buy these coins, artificially inflating their prices. Once the price reaches a certain level, scammers sell their holdings, causing the value to crash, and leaving other investors at a loss.
How to recognize and protect yourself
- Be cautious of sudden, unexplained spikes in cryptocurrency prices.
- Conduct thorough research before investing in any cryptocurrency.
- Avoid investing in projects with overly ambitious claims and unrealistic promises.
Impersonation scams
In this scam, scammers impersonate someone familiar, like a friend, family member, or an official organization. They use fake accounts and messages to request money, personal information, or sensitive data, taking advantage of trust.
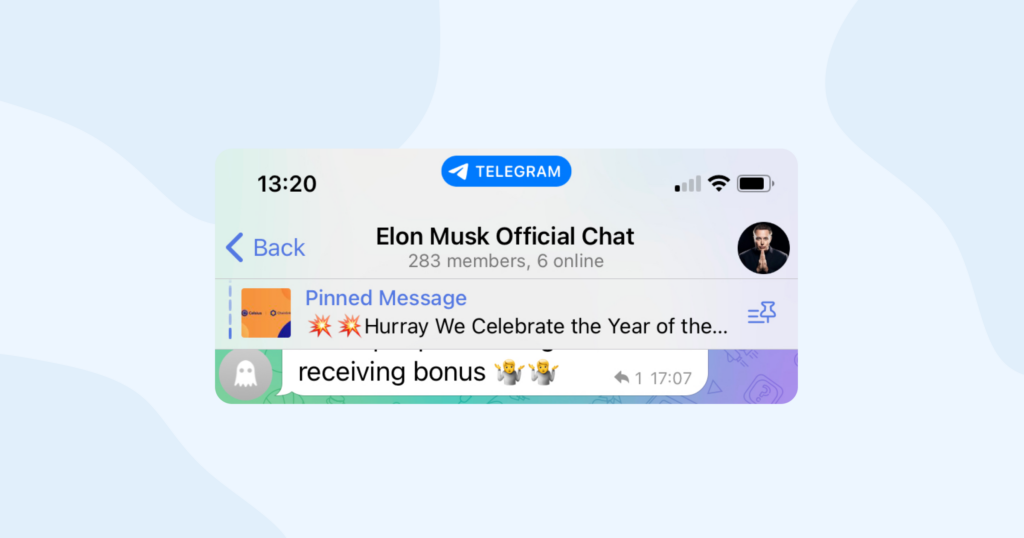
How to recognize and protect yourself
- Verify the identity of the person or organization by contacting them directly through known channels.
- Be cautious of urgent or unusual requests for money or personal information.
- Report suspicious accounts or messages to Telegram’s support team.
Malware distribution
Scammers may share seemingly harmless files (e.g., images, documents, or software) that contain malware. Once downloaded, the malware compromises the user’s device, allowing scammers to access personal data and sensitive information.
How to recognize and protect yourself
- Avoid downloading files from unknown sources.
- Use reliable antivirus software to protect against malware.
- Be cautious of messages with content that seems out of character for the sender.
Bogus ICOs (Initial Coin Offerings)
Scammers create fake ICOs for non-existent cryptocurrencies, enticing users to invest with the promise of high returns. However, after collecting funds, the scammers disappear, leaving investors with worthless tokens.
How to recognize and protect yourself
- Research the project and its team thoroughly before investing.
- Be wary of projects that lack a clear whitepaper or roadmap.
- Only invest in well-established and reputable ICOs.
Investment scams
In this scam, scammers advertise fake investment opportunities, promising high returns with little risk. Users are asked to send their funds to the scammer’s wallet, but the promised returns never materialize.
How to recognize and protect yourself
- Be cautious of unsolicited investment offers.
- Research the investment opportunity and the individuals involved.
- Seek advice from trusted financial advisors before making any investment.
Pyramid or Ponzi schemes
Pyramid schemes require participants to recruit others into the scheme, promising rewards for doing so. As the network expands, the structure becomes unsustainable, resulting in financial losses for those at the bottom.
How to recognize and protect yourself
- Be cautious of schemes that focus on recruitment rather than a legitimate product or service.
- Avoid schemes that promise high rewards with little effort.
- Remember that pyramid schemes are illegal in many jurisdictions.
Dating scams
Scammers create fake profiles on dating platforms and build trust with users. Eventually, they request money or gifts under false pretenses, preying on emotional vulnerability.
According to the US Federal Trade Commission, in 2022, approximately 70,000 individuals reported falling victim to romance scams, resulting in a staggering $1.3 billion in reported losses, with a median loss of $4,400.
How to recognize and protect yourself
- Be cautious of individuals who ask for money or expensive gifts early in a relationship.
- Avoid sharing sensitive information or images with people you have just met online.
- If suspicious, conduct a reverse image search to check the authenticity of profile pictures.
Tech support scams
In this scam, scammers pose as tech support personnel, claiming your device has issues that require immediate attention. They may ask for remote access to your device or demand payment to fix nonexistent problems.
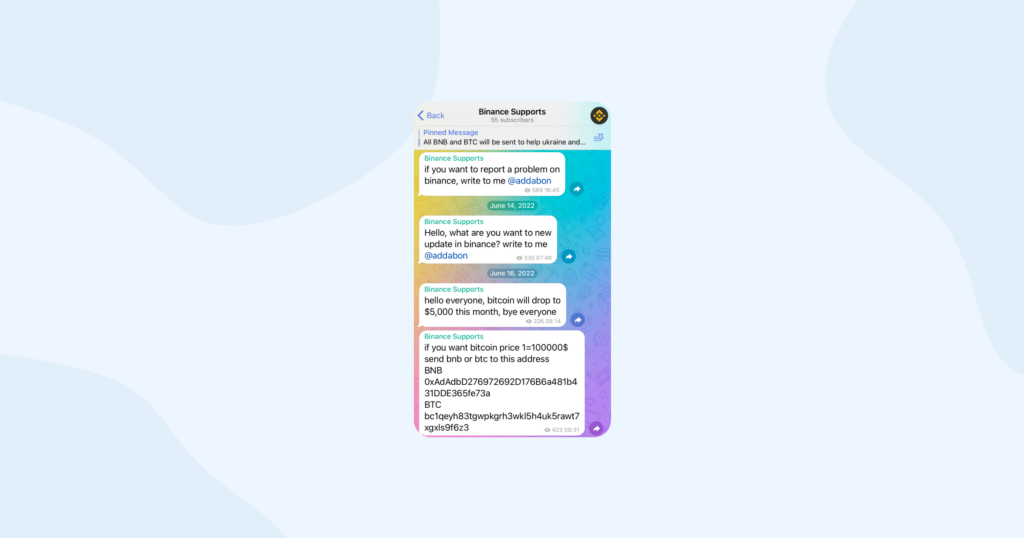
How to recognize and protect yourself
- Legitimate tech support will not contact you unsolicited. Be cautious of unexpected tech support messages.
- Verify the identity of the support representative and the company they claim to represent.
- Never give remote access to your device to someone you don’t trust.
Lottery scams
Scammers inform users that they have won a lottery or prize and request payment or personal information to claim the reward. In reality, there is no prize, and the user loses money or exposes personal data.
How to recognize and protect yourself
- Be skeptical of unexpected lottery wins or prizes you didn’t enter.
- Legitimate lotteries or contests do not require upfront payments to claim prizes.
- Never share personal information or financial details with unknown individuals.
5 golden rules to protect yourself from scammers
Following these rules can help you significantly reduce the risk of falling prey to scammers and maintain a safer online experience.
Rule 1: Be skeptical of unsolicited requests
Scammers often initiate contact through unsolicited messages, emails, or calls. Always approach such communications with caution, especially if they ask for personal information, money, or access to your devices. When in doubt, independently verify the legitimacy of the request before taking any action.
Rule 2: Verify identities and sources
Before sharing sensitive information, conducting transactions, or engaging in any financial activities, verify the identity of the person or organization you’re dealing with. Use official websites, phone numbers, or email addresses to cross-check the information you receive.
Rule 3: Educate yourself about common scams
Stay informed about the latest scam tactics and familiarize yourself with the typical red flags associated with scams. Knowledge is your best defense, and recognizing the signs of a potential scam can help you avoid falling into the trap.
Rule 4: Use strong passwords and enable 2FA
Protect your online accounts by using strong, unique passwords for each platform. Enable two-factor authentication (2FA) whenever possible, as it adds an extra layer of security, making it harder for scammers to gain unauthorized access.
Rule 5: Trust your instincts and seek help
If something feels off or too good to be true, trust your instincts and proceed with caution. Don’t hesitate to seek help or advice from trusted friends, family members, or professionals if you’re unsure about a situation. Reporting suspicious activities to relevant authorities or the platform involved can also help protect others from falling victim to the same scams.
TL;DR

Bottomline
In conclusion, Telegram scams pose a significant threat, with users collectively losing millions of dollars to fraudulent schemes (Source: [Specific Report or Research]). However, armed with knowledge and vigilance, you can protect yourself from falling victim to these deceptive tactics. Remember the five golden rules discussed in this article to fortify your online defenses.
For more insights on internet security and staying safe from cyber threats, check out this security guide.



